Whether you’re a seasoned guitarist or a beginner just starting out, changing your guitar strings is an essential skill that every player should master. Not
Category: Tech Tips

So you’re trying to decide between the RTX 2060 vs 3060 graphics cards, huh? I feel you. With so many GPU options out there nowadays,
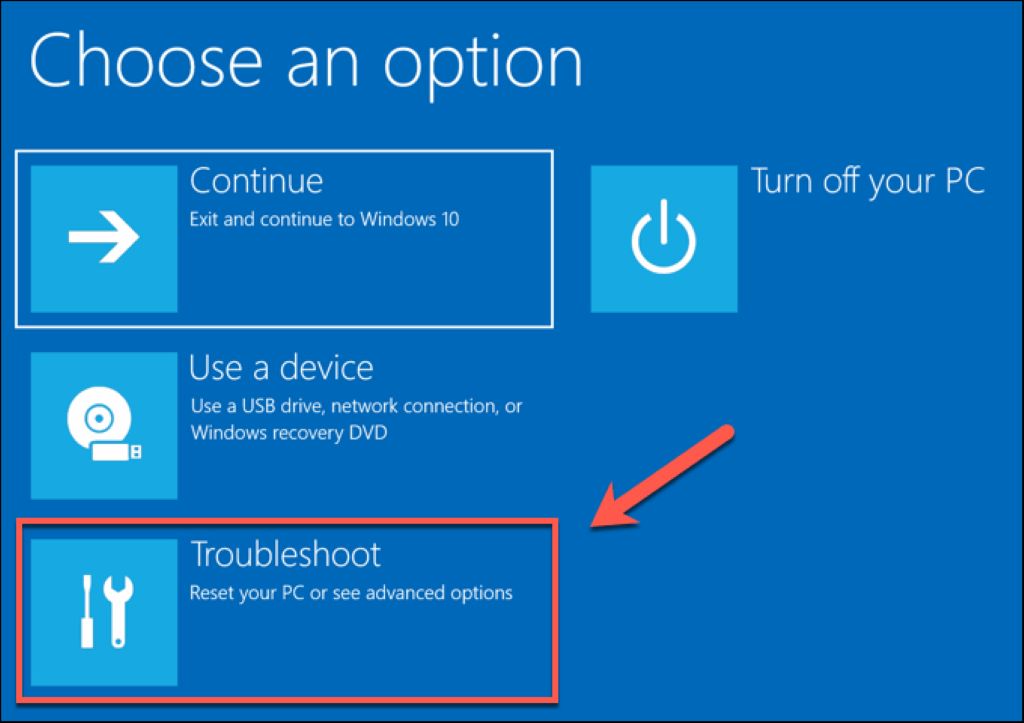
If you’ve ever found yourself facing the need to perform a factory reset on a device, you might have wondered: “Does a factory reset require

Are you tired of sluggish internet speeds on your 2.4 GHz WiFi network? Don’t worry, you’re not alone. Many of us rely on this frequency

Social media networks have seamlessly woven themselves into the fabric of our lives, altering the way we connect, communicate, and share. While they offer an

Imagine this: You’re working on an important project, and suddenly, your computer starts acting up. It’s slow, unresponsive, and you have no idea what’s wrong.

Are you a teacher who is no longer using certain classes in Google Classroom and wants to delete them? Deleting classes is a straightforward process

Did you know that Snapchat has dark mode? It’s true, and it’s super useful. You can use this feature to send dark themes on your

Linux aliases are convenient shortcuts for often-used commands. They can save you time and headache when typing out long or complicated command lines, but they’re

The game of Yugioh has been around for a very long time, and over the years, the game’s fans have come up with many ways

